
Executive Summary:
Below you will find an
example of an output from a
simple model Karsten Nohl (http://www.cs.virginia.edu/~kn5f/Mifare.Cryptanalysis.htm
) started as a threat modeling example for the Mifare transit card system.
The tool itself is interactive and is intended to
allow various stakeholders to attach to the model and build the tree. Here
is a screenshot of the original tool (the
output is a slight modification
from this original threat model).
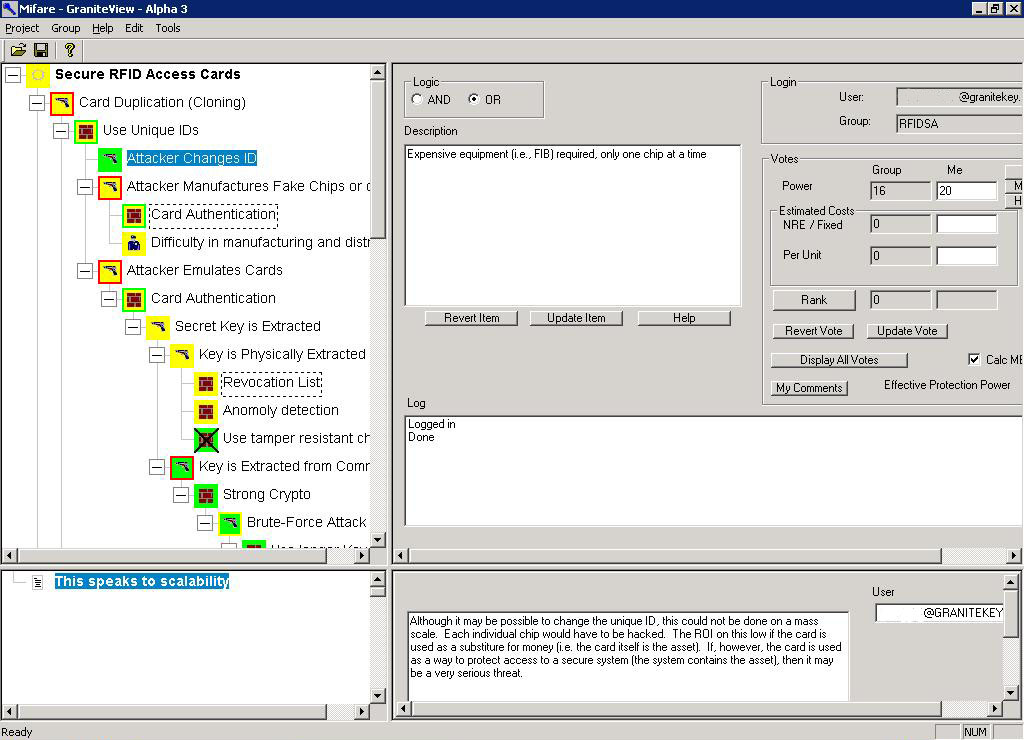
The structure of this threat model shall be as follows:
 Objective - What The Customer is trying to accomplish.
Objective - What The Customer is trying to accomplish.
 Threat - What is threatening The Customer's progress, business model,
livelihood.
Threat - What is threatening The Customer's progress, business model,
livelihood.
 Countermeasure - A countermeasure The Customer can introduce to address
threats.
Countermeasure - A countermeasure The Customer can introduce to address
threats.
 Process - A process The Customer can introduce to address threats.
Process - A process The Customer can introduce to address threats.
 Disabled - A threat, process, or countermeasure which has been disabled in
the model because it is either currently out of scope, or currently not
possible, or currently not being considered.
Disabled - A threat, process, or countermeasure which has been disabled in
the model because it is either currently out of scope, or currently not
possible, or currently not being considered.
The graphical icons are used to illustrate
varying levels of comfort and/or concern based on the power of the Threat,
Countermeasure, and Process:
-
Red illustrates a particularly grave situation.
-
Yellow illustrates a situation where caution should be taken.
-
Green illustrates an environment where security levels are well
controlled.
A Threat which is a high likelihood of
implementation, is highly scalable, or otherwise cause for great concern
would receive a red color coding. A Threat which is less likely to
occur, or may not be particularly feasible would receive a yellow, or even
green color coding. A Countermeasure or Process which would require
personnel to adhere to policies and distributed levels of trust of both
management and/or personnel would receive a yellow rating. The
intention of this exercise is to serve as a guideline for The Customer in
determining what decisions need to be made when implementing and integrating
security into the document/asset securing and tracking process. This should be considered an
evolutionary process which leads to improved security through the collaborative
examination of the Threat Model.
The top section of this Threat Model is
intended to give a summarized overview of the
Threat Hierarchy and has been structured
to link to portions of the Threat
Hierarchy, as well as external links which serve to further illustrate
and provide context where appropriate. Click on hyperlinks as you read
through the summary to move to the appropriate section.
 Objective: Secure RFID Access Card
System
Objective: Secure RFID Access Card
System
The top level objective of this model is to create
a RFID access card system which is secure.
 Card Duplication (Cloning)
Card Duplication (Cloning)
The access card can be duplicated to mimic an
unauthorized card
 Use Unique IDs
Use Unique IDs
Burn in
 Attacker Changes ID
Attacker Changes ID
Expensive equipment (i.e., FIB) required, only one chip at a time
COMMENT : [This speaks to scalability] Although it may be possible to change the unique ID, this could not be done on a mass scale. Each individual chip would have to be hacked. The ROI on this low if the card is used as a
substitute for money (i.e. the card itself is the asset). If, however, the card is used as a way to protect access to a secure system (the system contains the asset), then it may be a very serious threat.
 Attacker Manufactures Fake Chips
Or Cards
Attacker Manufactures Fake Chips
Or Cards
ID can be chosen arbitrarily or left programmable.
Only economical at large scale for popular cards (i.e., Mifare cards)
 Card Authentication [See
LINK Below]
Card Authentication [See
LINK Below]
Cryptographically authenticate card on each read
 Difficulty
In Manufacturing And Distribution In Volume
Difficulty
In Manufacturing And Distribution In Volume
 Attacker Emulates Cards
Attacker Emulates Cards
(a) on programmable cards -- Mifare SMX
(b) on a Laptop with RF frontend
COMMENT : Mark Schaeffer [What is Mifare SMX?] You can actually program one of their cards and create a clone?....
 Card Authentication
Card Authentication
Cryptographically authenticate card on each read
 Secret Key
Is Extracted
Secret Key
Is Extracted
 Key
Is Physically Extracted
Key
Is Physically Extracted
Expensive attack; requires physical access, breaks card, and only compromises one card at a time.
COMMENT : Mike Ahmadi [The extent of this threat depends on type of key.] If the key is
symmetric, then this is an extremely scalable and dangerous hack. If using
asymmetrical keys, then this is indeed less scalable.
COMMENT :
Mark Schaeffer [What kind of chip is this?] I assumed that this is
neither a secure EEPROM or Smart Card type of chip?
 Revocation List
[See LINK Below]
Revocation List
[See LINK Below]
Revoke reader keys that have been compromised.
Update revocation list on every tag read.
[time delayed measure]
COMMENT : Mark Schaeffer [Is there enough space on the card?] The problem with revocation lists is how large can they get and how secure is this list on the card.
COMMENT :
Mark Schaeffer [Operators must update list] We are relying on operators to update a list (i.e. generate a report when a reader is stolen). Also the assumption is that a reader can't be stolen, keys retrieved and then it is reinstalled over night
 Anomaly
Detection
Anomaly
Detection
If the same card is detected in 2 different locations (assuming different key for each card), it will revoke the card's validity in the database
COMMENT : Mark Schaeffer [This could be green] Eventually the cloned card would be detected
-
 Use
Tamper Resistant Chip
Use
Tamper Resistant Chip
expensive measure, not readily
available for RFIDs
COMMENT : Mark
Schaeffer [Removed because too expensive]
 Key is Extracted from Communication
Key is Extracted from Communication
Possible only when underlying cipher is weak (i.e., Mifare Crypto-1)
 Strong Crypto
Strong Crypto
Use stronger cryptographic function
 Brute-Force Attack
Finds Key
Brute-Force Attack
Finds Key
COMMENT : Mike Ahmadi [I would give a brute force attack a higher rating] Computers are getting faster and faster. This is a matter of disk space and raw horsepower, and that is getting cheaper every day.
COMMENT:
Mark Schaeffer [Use NIST recommendations] Although long term this is true, assume they are using NIST recommended crypto??
 Use
Longer Key
Use
Longer Key
Nothing above 64bits can be brute forced using current computers
COMMENT : Mike Ahmadi [Not today, perhaps]
 Time-Memory-Trade-Off Attacks
Time-Memory-Trade-Off Attacks
Attacker pre-computes (partial) code book to lookup keys. Large initial cost, but low cost for each compromised tag.
COMMENT : Mike Ahmadi [Can you explain this in more detail?]
COMMENT :
Mark Schaeffer [Yes, More info] I'd be interested in knowing if this is something that is used in practice and has implications across the applied crypto world in general (i.e. does this impact the assumption that anything recommended by NIST is OK)
 Diversify Crypto Function
Diversify Crypto Function
Integrate tag ID into encryption. Do so in a non-linear way.
This requires the attacker to pre-compute a different code book for each tag and hence takes away the advantage of time-memory trade-offs.
COMMENT : Mike Ahmadi [Explain this as well, please?]
 Credit
Information Stored In Database
Credit
Information Stored In Database
 Database Modification [See
LINK Below]
Database Modification [See
LINK Below]
The database of authorized identification information could be modified to contain unauthorized identification information..
 Tamper
With Turnstile/Reader To Let Invalid Cards In
Tamper
With Turnstile/Reader To Let Invalid Cards In
This involves not just skimming, but completely destroying the enforcement mechanism.
 Inspections,
Metal Boxes, Etc.
Inspections,
Metal Boxes, Etc.
 Reader
Access Cached Data
Reader
Access Cached Data
May allow cloned cards to work for some period (e.g. 24 hours)
 Reader Modification
Reader Modification
The card reader could be modified to accept RFID identification which is not authorized.
COMMENT : Mike Ahmadi [Requires More Effort] It is likely that modifying the reader will require more effort that modifying or cloning the access card.
COMMENT :
Mark Schaeffer [What kind of access does a hacker have?] I would have to see the setup. Offhand, it seems that a hacker breaking into a public transit turnstile is unlikely. If they could get access to change the reader, how much more difficult is it to just disable the whole thing so it lets anybody though.
 Skimming Device
Skimming Device
In light of the recent proliferation of skimming devices which
have been covertly placed in ATM readers, it may be possible for an
attacker to add a skimming device to the RFID reading device which could
capture information which an attacker could use to create an exploit.
COMMENT : Mike Ahmadi [I think skimming devices are a huge threat.] Now that you can find skimming devices all over the web (http://www.hackaday.com/2006/05/01/portable-magnetic-card-reader/), I would give this a much higher threat rating
 Anti-Tampering Mechanism
Anti-Tampering Mechanism
An anti-tampering mechanism could be added to the reader to indicate that the reader has been breached.
 Tamper Indicating Seal
Tamper Indicating Seal
The anti-tampering
mechanism could consist of a seal which indicates that the device has been tampered with.
 Clone Seal
Clone Seal
The Tamper Indicating Seal could be cloned and a duplicate replacement could be used in its place after breaching the system.
 Use a Seal With Difficult To Duplicate Features
Use a Seal With Difficult To Duplicate Features
The seal can contain difficult to duplicate features, such as color shifting ink, micro-printing, holograms, etc.
 Human Monitoring [See
LINK Below]
Human Monitoring [See
LINK Below]
A person or persons can have the responsibility of constantly monitoring the reader to make sure nobody unauthorized modifies it.
 Human Monitoring
Human Monitoring
A person or persons can have the responsibility of constantly monitoring the reader to make sure nobody unauthorized modifies it.
 Complacency
Complacency
The people monitoring the device become complacent.
COMMENT : Mike Ahmadi [Dull Jobs Cause Complacency] Despite the best intentions of the people in charge of guarding an asset/system, the brain eventually tires and, within a short time, can no longer see a problem it once could. The mind effectively becomes numb (http://news.bbc.co.uk/2/hi/science/nature/7358863.stm)
 Corruption
Corruption
The people monitoring the device 'turn a blind eye' due to corruption (lack of ethics).
 Reader Authentication, Encryption
Reader Authentication, Encryption
Enable the card to verify the authenticity of the reader.
On sucessfull authentication, the authentication data can be used as session key for data encryption.
 Attacker Extracts Secret Keys
Attacker Extracts Secret Keys
A reader is stolen and its secret keys are extracted, thereby enabling the attacker to build a skimming device that is indistinguishable from a
legitimate reader.
 Tamper-Resistant Hardware
Tamper-Resistant Hardware
Encrypt keys in hardware TPM or other security chip; make TPM erase keys when hardware is opened
 Revocation List
Revocation List
Revoke reader keys that have been compromised.
Update revocation list on every tag read.
[time delayed measure]
COMMENT : Mark Schaeffer [Is there enough space on the card?] The problem with revocation lists is how large can they get and how secure is this list on the card.
COMMENT :
Mark Schaeffer [Operators must update list] We are relying on operators to update a list (i.e. generate a report when a reader is stolen). Also the assumption is that a reader can't be stolen, keys retrieved and then it is reinstalled over night
 Attacker Blocks List Propagation
Attacker Blocks List Propagation
If
sufficiently many reader are replaced with skimming devices, the attacker can prevent the revocation lists to be updated on the cards.
COMMENT : Mike Ahmadi [This needs some clarification] Can you explain how this works?
 Steal
Keys From Card Instead Of Reader
Steal
Keys From Card Instead Of Reader
 Use
Asymmetrical Encryption
Use
Asymmetrical Encryption
Do NOT use a master key everywhere
 Corrupted Path to Database
Corrupted Path to Database
Attacker reads or alters communication between reader and database
COMMENT : Mike Ahmadi [This is a very serious threat.]
 Mutual Authentication between Reader and Database
Mutual Authentication between Reader and Database
Use cryptographically-secured channel for communication.
 Attacker Extracts Secret Keys [See
LINK Above]
Attacker Extracts Secret Keys [See
LINK Above]
A reader is stolen and its secret keys are extracted, thereby enabling the attacker to build a skimming device that is indistinguishable from a
legitimate reader.
 Database Modification
Database Modification
The database of authorized identification information could be modified to contain unauthorized identification information..
 Proxy Attack
Proxy Attack
Attacker tunnels data between legitimate card and reader; potentially over large distances
COMMENT :
Mark Schaeffer [Please explain]
 Distance Bounding Protocol
Distance Bounding Protocol
Cryptographic real-time protocol that allows reader and tag to measure communication distance
-
 Secret Key is Extracted [See
LINK Above]
Secret Key is Extracted [See
LINK Above]

Objective - What The Customer is trying to accomplish.
Threat - What is threatening The Customer's progress, business model,
livelihood.
Countermeasure - A countermeasure The Customer can introduce to address
threats.
Process - A process The Customer can introduce to address threats.
Disabled - A threat, process, or countermeasure which has been disabled in
the model because it is either currently out of scope, or currently not
possible, or currently not being considered.